A VPN is usually a good way to keep your online activities private from your ISP and other prying eyes. That’s why it’s a popular security tool amongst both individuals and organizations. However, it’s not always 100% foolproof. Some VPNs’ vulnerabilities can be exploited by hackers.
That’s what happened with two popular VPN services Fortigate SSL and Pulse Secure SSL, researchers at Devcore reported last month. They presented five security vulnerabilities discovered during an assessment and a Chinese hacker group ATP5 has targeted the two services just a few days ago, following the disclosure of these findings.
What’s happened?
The Devcore team studied the SSL VPNs. The research showed that the vulnerabilities discovered can make it possible for hackers to steal and change passwords remotely. The Chicago-based intelligence company Bad Pockets performed some scans with its honeypots and discovered that over 14,500 vulnerable endpoints were belonging to Pulse Secure.
The malicious activity of mass scanning was reported to originate from Spain. The Pulse vulnerabilities’ further exploitation, in addition to the risks outlined above, can lead to remote injection of malicious commands and give hackers access to the VPN network. The vulnerabilities were found in the servers in 121 countries, USA and Japan amongst the most affected.
The same breach has taken place a few days later with Fortigate – Bad Pockets detected malicious activity attempting to download usernames associated with the server. This activity has allegedly originated from the US. The Information Security Newspaper reports that the flaw was in the authentication method which allowed hackers to change passwords.
These flaws in the security system are significant. If undetected and unrectified, they can affect software required to be accessible to the Internet and act as a key to an internal network of an organization.
The IP addresses of the affected endpoints were autonomous systems belonging to organizations such as the US government and military, healthcare providers, major financial institutions, universities, and large Fortune 500 companies. The exact list is not disclosed, due to the vulnerability’s ease of exploitation with the help of an open-source proof-of-concept code available on GitHub.
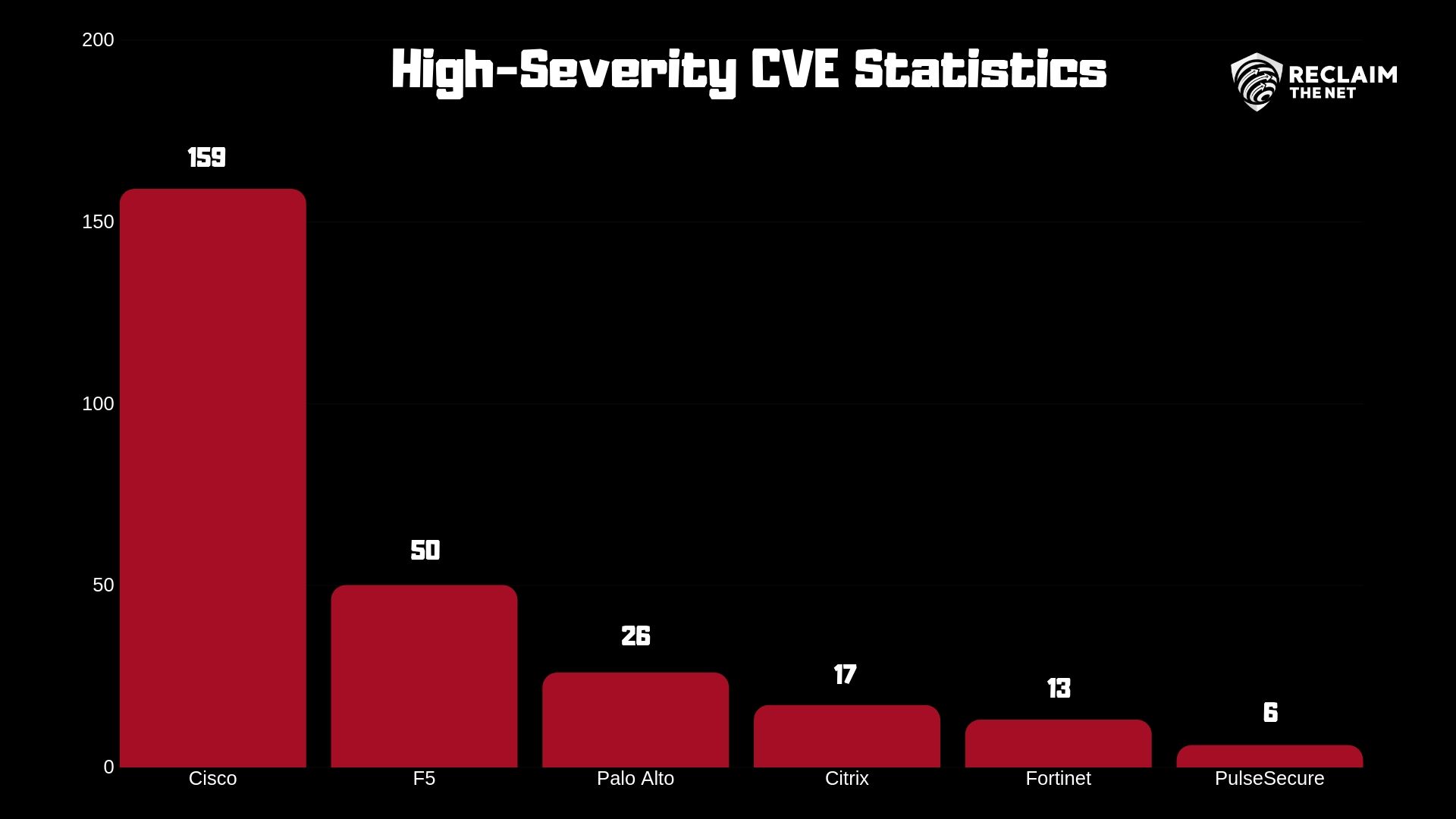
This isn’t the first time these VPNs have faced the issue of security flaws. Devcore has first reported the gaps in Fortigate’s system last year and in Pulse in March of this year. This was done during a study initiated a little over a year ago by Devcore conducted to test SSL-based VPNs’ security. The statistics below are what prompted them to test Fortigate and Pulse and discover the vulnerabilities.
ATP5 group has taken advantage of the weaknesses in the VPN systems by scanning for vulnerable servers, but it’s not known for certain whether they have succeeded. The danger, however, is very obvious and relevant, given the popularity of the two services.
If a VPN network is hacked and third parties gain access, it effectively renders a VPN service useless. You pay money for your online behaviors to be secure and rely on a VPN service to protect your data. Such a breach can be devastating for both a person and a company that relies on a corporate VPN.
I’ve previously written about why you should be using a VPN at all times, and I can understand the anxiety stemming from hearing about such breaches. After all, data is one of the most valuable assets a person or a business can have in this day and age.
By providing hackers with an opportunity to change passwords, a VPN service would leave a user’s data vulnerable to theft, modifications, and exploitation for all kinds of nefarious purposes.
What can be done now?
Both Fortigate and Pulse Secure thanked the Devcore researchers by publishing advisory information on their websites about the security flaws (Fortigate did so back in May after they received Devcore’s initial findings).
The users of the two services should patch their VPN packages and install the relevant updates within the shortest possible convenience to avoid any data being leaked. The researchers have also reportedly shared their findings with law enforcement agencies.
If you're tired of censorship and dystopian threats against civil liberties, subscribe to Reclaim The Net.