The core team working on privacy-focused cryptocurrency Monero has admitted that the code available for download on GetMonero.org may have been compromised at some point during the last 24 hours. Despite the admission, no official warning has been posted to GetMonero.org to let users know that they may be unknowingly running code that could steal their cryptocurrency.
The compromised code was discovered by a user on GitHub. The Monero core team then confirmed on Reddit and Twitter that the code may have been compromised and advised users who had run the code without verifying the integrity of the files to empty their wallets because of the “probably malicious” executable code:
“If you downloaded binaries in the last 24h, and did not check the integrity of the files, do it immediately. If the hashes do not match, do NOT run what you downloaded. If you have already run them, transfer the funds out of all wallets that you opened with the (probably malicious) executables immediately, using a safe version of the Monero wallet (the one online as we speak is safe but check the hashes).”
Other users on GitHub and Reddit have also suggested that the compromised code is stealing cryptocurrency and security researchers are in the process of further investigating these claims:
“I can confirm that the malicious binary is stealing coins. Roughly 9 hours after I ran the binary a single transaction drained the wallet. I downloaded the build yesterday around 6pm Pacific time.”
While users on Reddit, Twitter, and GitHub may have seen these warnings, there are no similar warnings on GetMonero.org – the website which served this compromised code. The website does contain a reminder that encourages users to make sure their software is up-to-date and links to a 10-day old Reddit thread but there is no mention of the code being compromised over the last 24 hours.
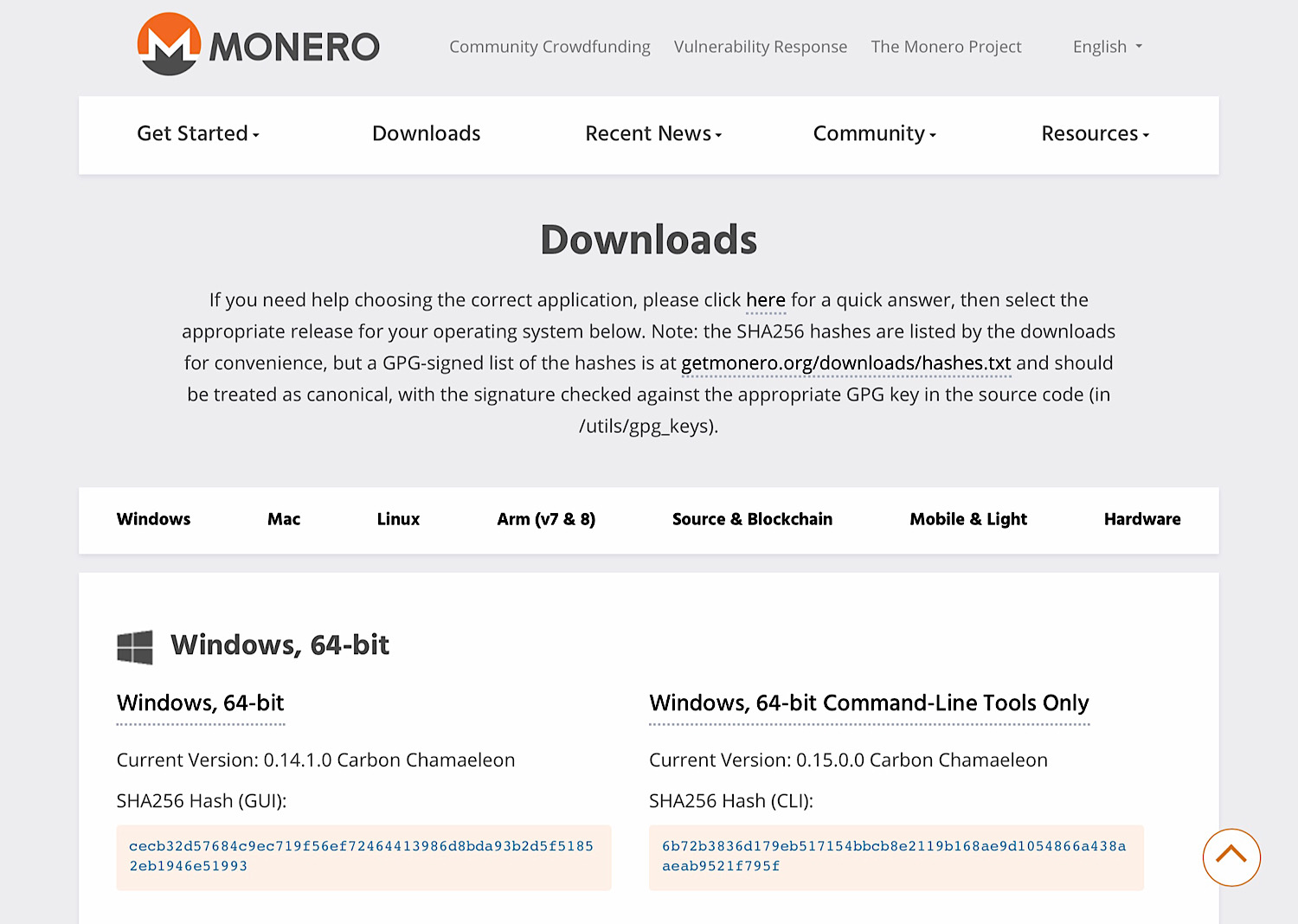
This means users who downloaded the code but don’t follow the Monero team on other platforms may be unknowingly putting their Monero at risk of being stolen by running coin stealing malware.
Some Twitter users have called for Monero to post a warning to the official website and download page:
Click here to display content from X.
Learn more in X’s privacy policy.
However, Monero isn’t currently responding to these requests and is only posting updates about the situation to Reddit, Twitter, and GitHub.