Google is often widely criticized for violating its users’ privacy by virtue of being a dominant and centralized service in control of data belonging to millions of people – and willing to use this data as a business model.
But sometimes it also plays fast and loose with their privacy inadvertently – one example being a recently discovered bug in Google Photos that would have made it possible for bad actors to find out the location and date of creation of the pictures users upload to the service.
Bleeping Computer is reporting that the vulnerability – that has since been fixed – affected the web version of the app, and specifies that the bug could have let websites find out a user’s location history based on the photos.
The flaw was discovered by Imperva Researchers, who announced that it could have been used by malicious websites, exploiting Google’s powerful search and artificial intelligence functions, to expose “where, when, and with whom your photos were taken.”
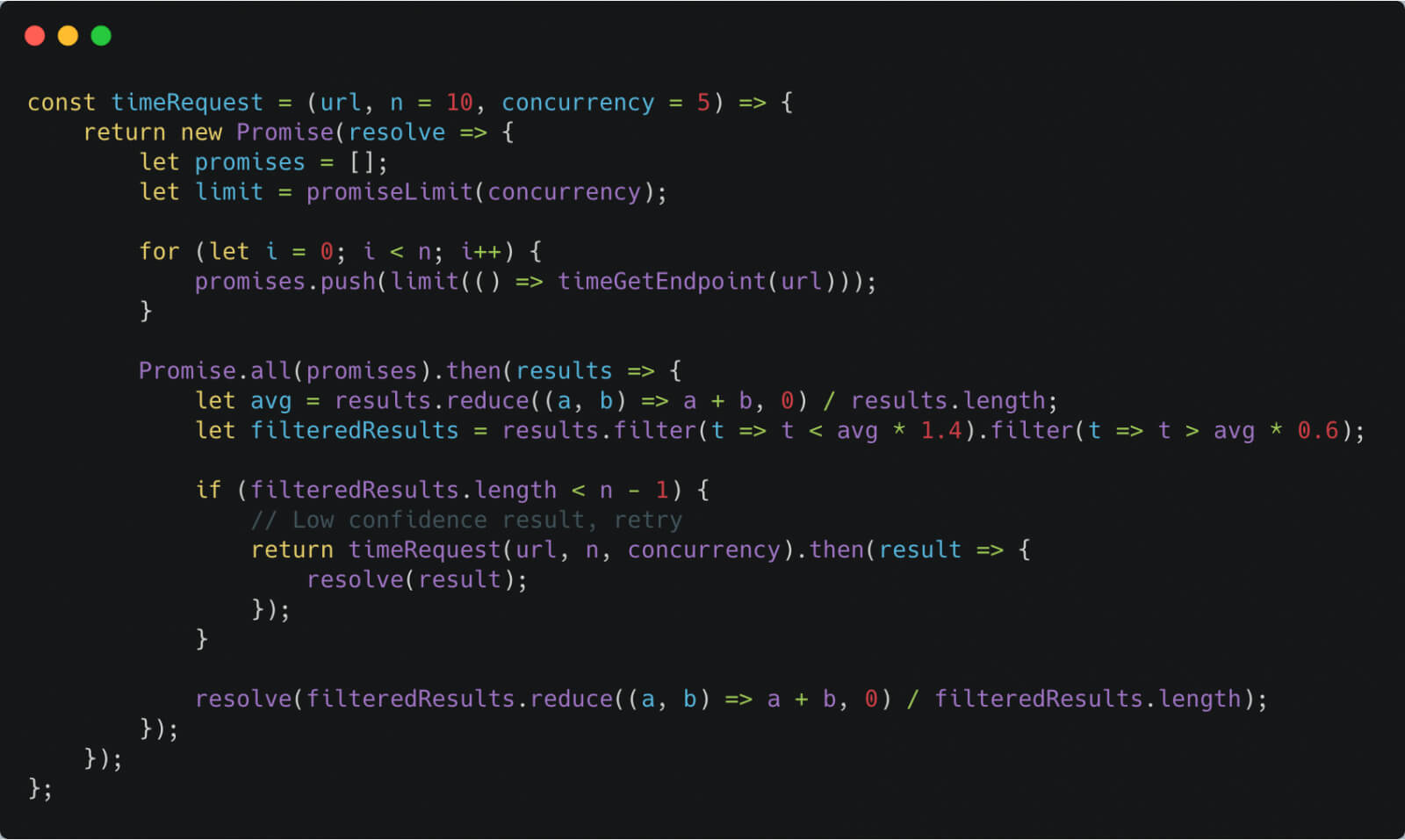
Imperva security researcher Ron Masas’ proof-of-concept showed that the photos’ metadata could be discovered by taking advantage of the flaw, which affected the Google Photos search endpoint, which works by using aggregated metadata.
He explained that he used the HTML link tag to create multiple cross-origin requests to the search endpoint, and then JavaScript to measured “the amount of time it took for the ‘onload’ event to trigger.”
In order to become of a victim of hackers bent on retrieving metadata from their photos, a user would have to be logged into their Google Photos account – accomplished automatically by signing into any Google service – and simultaneously lured into visiting a malicious website – either directly or through a spot of social engineering.
The malicious JavaScript code would then silently create requests to the Google Photos search endpoint, “extracting Boolean answers to any query the attacker wants,” the researcher writes.
Previously, Masas discovered a similar browser side-channel attack in Facebook Messenger that allowed websites to expose who the user had been exchanging messages with.
This type of attack – which Masas describes as stoill an overlooked subject – works best when targeting a specific individual in order to spy on their online activities, but is less useful in a mass data collection scenario.
For a video overview of the leak, there’s a YouTube video from Bleeping Computer here.