A database of a Chinese dating app targeting U.S users was discovered online by the security researcher Jeremiah Fowler.
According to his report on Security Discovery, the database wasn’t password protected and had no security measures in place. It is reported that this database had exposed over 40 million user records mined from several dating applications. The details exposed include users’ IP addresses, age, usernames, and geolocation data.
According to Fowler’s report, he came across the unprotected database with Chinese text and all the dating apps mentioned in the database were easily found through a simple Google search.
The security researcher said that all the dating apps were sharing the same database but had, however, claimed to be developed by separate entities or individuals. It was also found that there was no easy matchup or a relation between these dating apps whose data was found in the database.
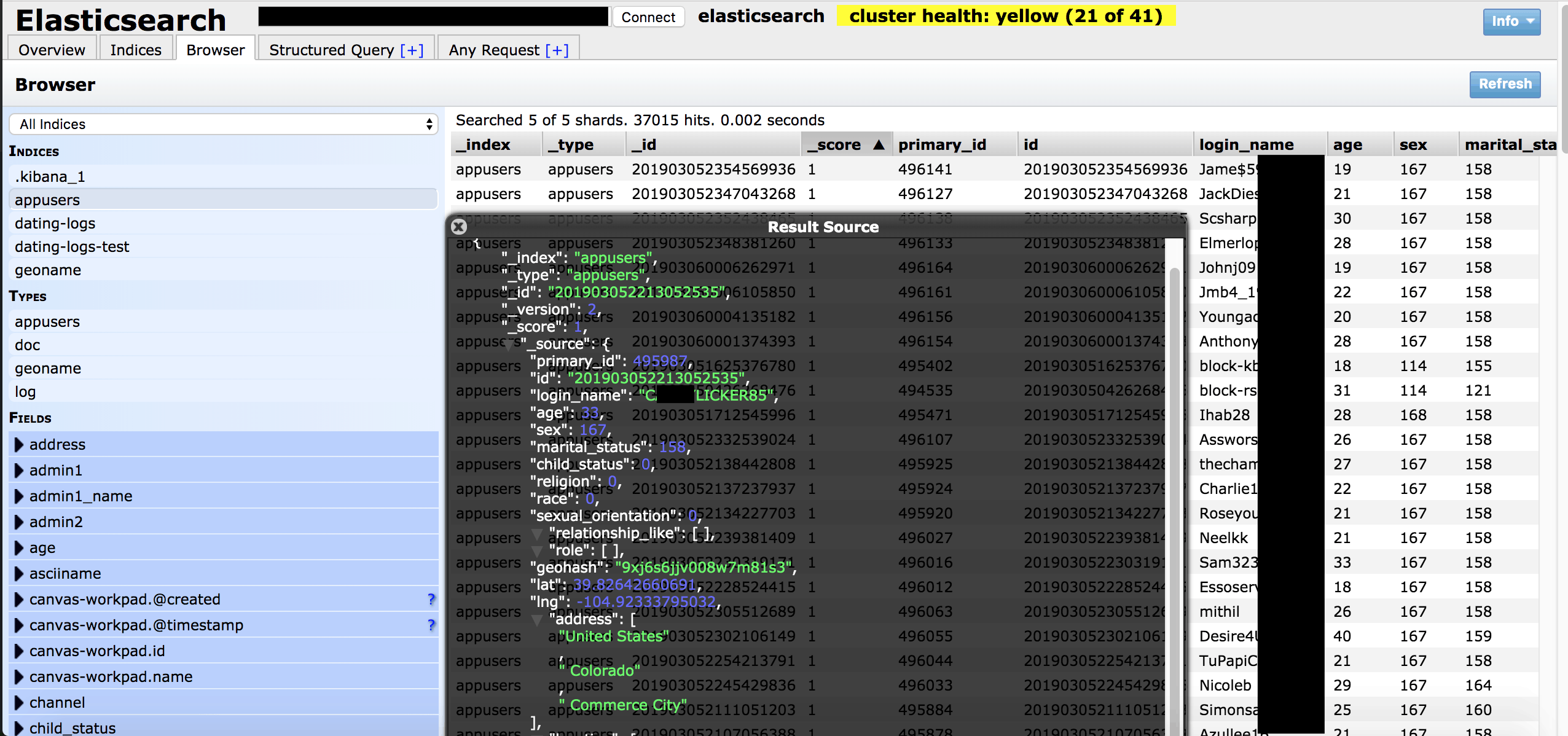
Upon performing a Whois search, it was revealed that most of the companies had been registered as private entities and reaching out to them was only possible through their app. Fowler said that one of the sites seemed to display a fake identity on the Whois search. It was however reported to be exceedingly simple for identifying and locating the individuals mentioned in the database.
Here are some apps mentioned in the database:
● Cougardating (an app for meeting cougars and spirited young men)
● Christainsfinder (an app for single Christians to find an ideal match online)
● Fwbs (Friends with benefits)
● Mingler (interracial dating app)
As a part of responsible disclosure, Security Discovery did try reaching out to the apps by sending two emails to the email accounts linked to the domain registration of some of the dating sites. While there was one seemingly genuine lead from the Whois search of a site, it was later found that the phone number was all 9s and the address is of a metro station.
It raises suspicion to see that the app developers and website owners have gone to such lengths for concealing their real identity. As of now, the database still remains unsecured online.













