Following the arrest of Telegram CEO Pavel Durov, attention from individual citizens, to the media, to nation states has been focused on the app and the nature of its encryption and privacy.
Telegram, which boasts almost a billion users, bills itself as an encrypted messaging app and, while this is true, understanding the app’s privacy requires a little more nuance, especially following Durov’s arrest.
The term “encryption” is often used broadly, but in the realm of private messaging services, it usually implies a specific standard: default end-to-end encryption.
There are Two Main Types of Encryption:
Non-End-to-End Encryption (Cloud Encryption)

In non-end-to-end encryption, messages are encrypted by the sender, but the encryption keys needed to decrypt the messages are accessible to the service provider. This means that while the messages are protected during transmission (over the internet), once they reach the service provider’s servers, the provider can decrypt and access the content of the messages. This setup is common in services where the provider might need to access message content for various reasons, such as indexing for search, applying spam filters, or complying with legal requests.
For example, Gmail uses this type of encryption. When you send an email via Gmail, it is encrypted during transit, ensuring that interceptors cannot read it. However, once your email reaches Google’s servers, Google has the capability to decrypt the emails. This is because Google controls the encryption keys. This capability allows Google to scan emails for spam and malware, provide search functionality across your emails, and comply with legal demands such as subpoenas or warrants that require access to email content.
End-to-end Encryption

Conversely, with end-to-end encryption, the data (such as messages or calls) are encrypted on the sender’s device and only the intended recipient has the key to decrypt it. This means no intermediary, not even the service provider, has access to the encryption keys necessary to decrypt the data. The message stays encrypted throughout its journey from sender to receiver, becoming readable only when it reaches its intended destination.
When you send a message via these platforms, nobody besides you and the recipient—not even the companies running these services—can read what’s sent. This secures your communication against both cyber threats and any potential surveillance from service providers or government authorities, making it a stronger option for protecting privacy.
Telegram employs a hybrid approach to encryption, incorporating both non-end-to-end encryption for general messages and an optional end-to-end encryption feature for those seeking higher security.
For the majority of its user interactions, Telegram does NOT use end-to-end encryption.
Under this system, messages are encrypted on the sender’s device and sent to Telegram’s servers where they are stored.
Telegram’s non-end-to-end encryption is employed across several of its key features:
Multi-device Access: Users can access their messages from multiple devices simultaneously. Since messages are stored on Telegram’s servers after being encrypted, users can seamlessly sync their chat histories across any number of devices, such as smartphones, tablets, or computers.
Chat Backups: Telegram provides the ability to restore your chat history when you switch to a new device. This is possible because the messages are stored in the cloud, ensuring that no data is lost even if your device is.
Large Group Chats and Channels: Telegram’s cloud encryption facilitates the management of large group chats and channels, which can include thousands of members. This setup allows for efficient delivery and storage of messages even in large volumes.
Bot Integration: Bots on Telegram can interact with users in various ways, such as by sending customized notifications, facilitating transactions, or providing information services. These bots can access messages sent to them by users because those messages are not end-to-end encrypted.
These features are supported by the fact that Telegram can, in theory, decrypt and manage messages as needed, thanks to the company having access to the encryption keys.
In a statement addressing its encryption practices, Telegram outlined its unique approach. “Cloud Chat data is stored in multiple data centers around the globe, controlled by different legal entities across various jurisdictions,” Telegram explained. The company further alleged that decryption keys are split into parts and kept separate from the data they protect, making unauthorized access by local engineers or intruders virtually impossible. “As a result, local intruders or engineers can’t access this data, and several court orders from different jurisdictions are required to force us to give up any of it,” the statement continued.
In summary, when you start a standard chat or group chat with someone on Telegram, your chat is NOT end-to-end encrypted and can, in theory, be decrypted by an entity other than you and the recipient of your messages.
When you follow a channel on Telegram, this is more like social media and the data transmitted there is also NOT end-to-end encrypted. In fact, it can even be visible on the open web like this.
However, Telegram does offer an end-to-end encrypted feature with what it calls “Secret Chats.” This mode of communication is protected by end-to-end encryption, in theory ensuring that only the communicating parties—the sender and the recipient—can read the messages. In this mode, Telegram says nothing is stored on Telegram’s servers, and there are no keys available to Telegram or any third parties. Secret Chats also include additional security features like self-destructing messages and screenshot notifications which let you know when someone has screenshotted a message in your Secret Chat.
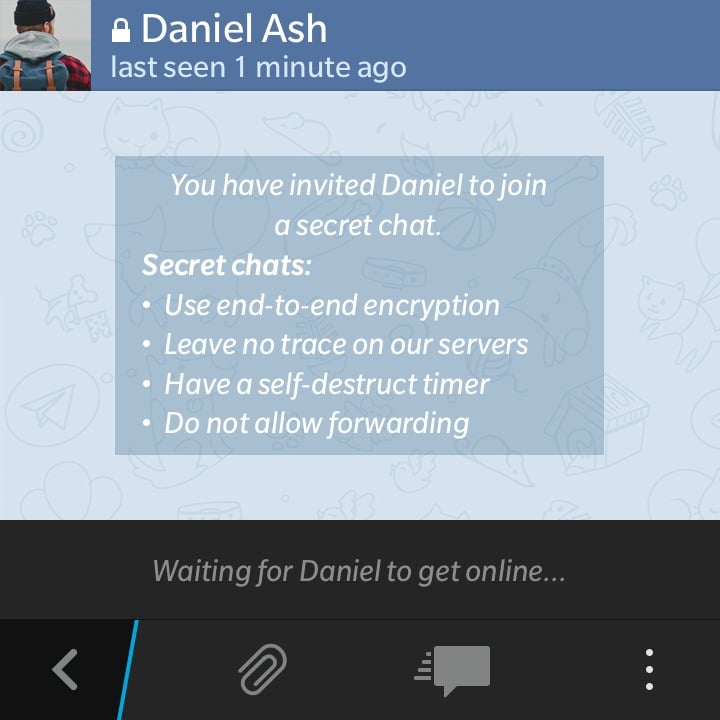
Note that Secret Chats need to be activated manually for each conversation and are only available for one-on-one chats. This means that if users do not specifically opt for Secret Chats, their communications are not protected by end-to-end encryption.
While Secret Chats have a high level of security, they are less convenient than standard chats because both participants must be online for Secret Chats to initiate and exchange encrypted messages. Secret Chats also remain on the devices that they were initiated from and cannot be synced to the users’ other devices.
Different Types of End-To-End Encryption
For simplicity’s sake, there are two basic forms of end-to-end encryption – open source, and closed source.
Open Source Encryption

Open-source encryption is widely regarded by cybersecurity experts as one of the most secure methods of encryption. This preference is rooted in the transparency and community scrutiny that open-source projects afford. When encryption software is open source, its source code is publicly available, allowing anyone to examine how the software functions and verify the security of its encryption methods.
Transparency and Security Audits: One of the primary advantages of open-source encryption is the level of transparency it provides. Since the source code is accessible to all, independent security experts, researchers, and developers can scrutinize it for vulnerabilities, flaws, or backdoors. This continuous and open vetting process tends to result in more secure software, as issues are identified and, in theory, patched more quickly compared to proprietary software, where the code is only accessible to the company’s internal team.
Community Collaboration: Open source projects benefit from the collective expertise of a global community. Developers from around the world can contribute to the project, enhancing the software with new features, security enhancements, and fixes. This collaborative approach not only speeds up the development and fortification of the software but also fosters innovation within the field of encryption.
Building Trust Through Transparency: For encryption software, trust is paramount. Users need to trust that the software will protect their data as claimed. Open-source encryption builds trust through its transparency—users don’t need to rely on the security claims of a vendor; they can see for themselves or rely on the assessment of independent experts who have reviewed the code.
Closed-Source Encryption

Most experts caution against the use of closed-source encryption due to its lack of transparency, which can obscure potential vulnerabilities and limit external verification. Unlike open-source encryption, where the code is available for public review, closed-source encryption keeps its operational code hidden, restricting the assessment of its security to the internal teams of the company that owns it. This secrecy can prevent independent security experts from conducting thorough audits, making it harder to trust the encryption’s robustness. Additionally, without external scrutiny, it’s more challenging to identify and rectify security flaws, which could potentially leave user data at risk of unauthorized access or breaches.
When using closed-source encryption, requires more trust as the claims about the degree to which communications are encrypted can’t be independently verified.
Telegram’s end-to-end encryption is closed source which has raised skepticism within the security community.
Telegram has given several reasons for its approach. The company emphasizes the balance between user convenience and security. Telegram’s founder, Pavel Durov, has alleged that making the entire platform open-source could potentially expose it to more risks, as malicious actors might find it easier to spot vulnerabilities and exploit them.
Telegram has also argued that its in-house-developed encryption and security processes are robust and secure, even without the open-source model. It claims that its internal security team continuously works on enhancing the security features, maintaining that the security of Telegram’s encrypted data—both for cloud chats and for secret chats—meets high standards even without external validation.
When choosing between open-source and closed-source encryption tools, it’s crucial for individuals to make informed decisions based on a clear understanding of the differences associated with each approach. Open-source encryption offers greater transparency, allowing anyone to independently scrutinize and verify the security of the software and verify that a company is doing what it says it is, which can lead to enhanced trust and security through collective improvements. On the other hand, closed-source encryption requires more trust, does not provide the same level of transparency and external audits, and makes it more difficult to assess the tool’s security.
Understanding these key differences is essential because the choice of encryption tool can significantly impact the security of your communication and data.
Consider Metadata

However, that’s not the full story. Another important aspect to consider is what is being done with the data that is collected.
WhatsApp, Facebook Messenger, and Telegram are among the most widely used messaging apps globally, each with its own approach to user privacy and data security.
WhatsApp and Facebook Messenger, both owned by Big Tech giant Meta, offer end-to-end encryption for conversations between users, ensuring that the content of messages is protected from interception. However, these platforms do collect and store metadata, which includes information about who communicates with whom. This data is subject to US jurisdiction and can be accessed by government authorities through legal channels, meaning that while the content of the messages remains private, the patterns of communication are not private.
Some of Meta’s platforms, such as Facebook and Instagram, also collect vast amounts of data about users outside of these end-to-end encrypted conversations. Since Meta’s platforms share data with each other, Meta also has the capability to create and share revealing user profiles that extend beyond these patterns of communication.
Telegram, on the other hand, with its mixed model where only the “Secret Chats” are end-to-end encrypted, means that regular messages are encrypted but not end-to-end, leaving them accessible under certain conditions. Although Telegram also collects some user data, it has a history of being more resistant to government requests for data access and content censorship, at least as far as the public is aware. Part of Durov’s arrest in France is predicated on Telegram’s refusal to comply with government requests.
While this requires a lot of trust, this stance is why some see Telegram as a strong choice for those seeking more privacy from government oversight, particularly in regions with stringent control over digital communications.
The arrest of Durov is particularly concerning in this context. Durov’s reported commitment to resisting government intrusion and censorship has been a cornerstone of Telegram’s policy, making his arrest a significant alarm for advocates of digital privacy and freedom of expression.
This arrest raises concerns about the future direction of Telegram’s privacy policies and its ability to resist external pressures, potentially affecting the trust and reliance users place on the platform for secure communications.



