Poor security practices and the presence of a large number of third-party tracking services on their websites means that as many as two thirds of hotels around the world could leak sensitive personal data of their customers, Symantec has discovered.
Candid Wueest, principal threat researcher with the California-based cybersecurity firm, said in a company blog post that the 1,500 hotels located in 54 countries included in the test ranged from two- to five-star establishments. Regardless of the privacy policy they have in place, 67 percent of these hotels “inadvertently” leak booking reference codes to about a total of 30 advertisers, social networks, search engines, and analytics services.
The personal data exposed in this way ranges from customers’ names, postal and email addresses, phone numbers, last four digits of their credit cards, including card type and expiration date, to passport numbers ZDNet is reporting, citing the security blog post.
The vulnerability exists thanks to the hotels’ booking websites sending unencrypted links to customers and leaking credentials as URL arguments, which then become available to third party services, allowing them to view personal data, log into reservations, or cancel them – to harm either the travelers, or the establishments’ reputation.
The issue is all the more grave as it has been discovered nearly one year after EU’s General Data Protection Regulation (GDPR) came into force, designed to counter precisely such scenarios – highlighting once again that companies are either struggling with implementation, or not even trying hard enough.
Symantec suggests that the latter may be the case with the hotels affected here, as their response to the report of the problem has been “disappointing.” 25 percent of data privacy officers the security firm informed of the problem did not respond even after six weeks, while those who did took ten days on average, mostly to tell the researcher that they were now aware of the issue and would work to fix it. There were also those who said the leaked data was “not personal at all” – and that it “has to be shared with advertising companies as stated in the privacy policy.”
Symantec observed that while customers can check if links sent to them are encrypted – “for the average hotel guest, spotting such leaks may not be an easy task, and they may not have much choice if they want to book a specific hotel.”
Recently, IP and tech lawyer, Annemarie Bridy, posted on Twitter:
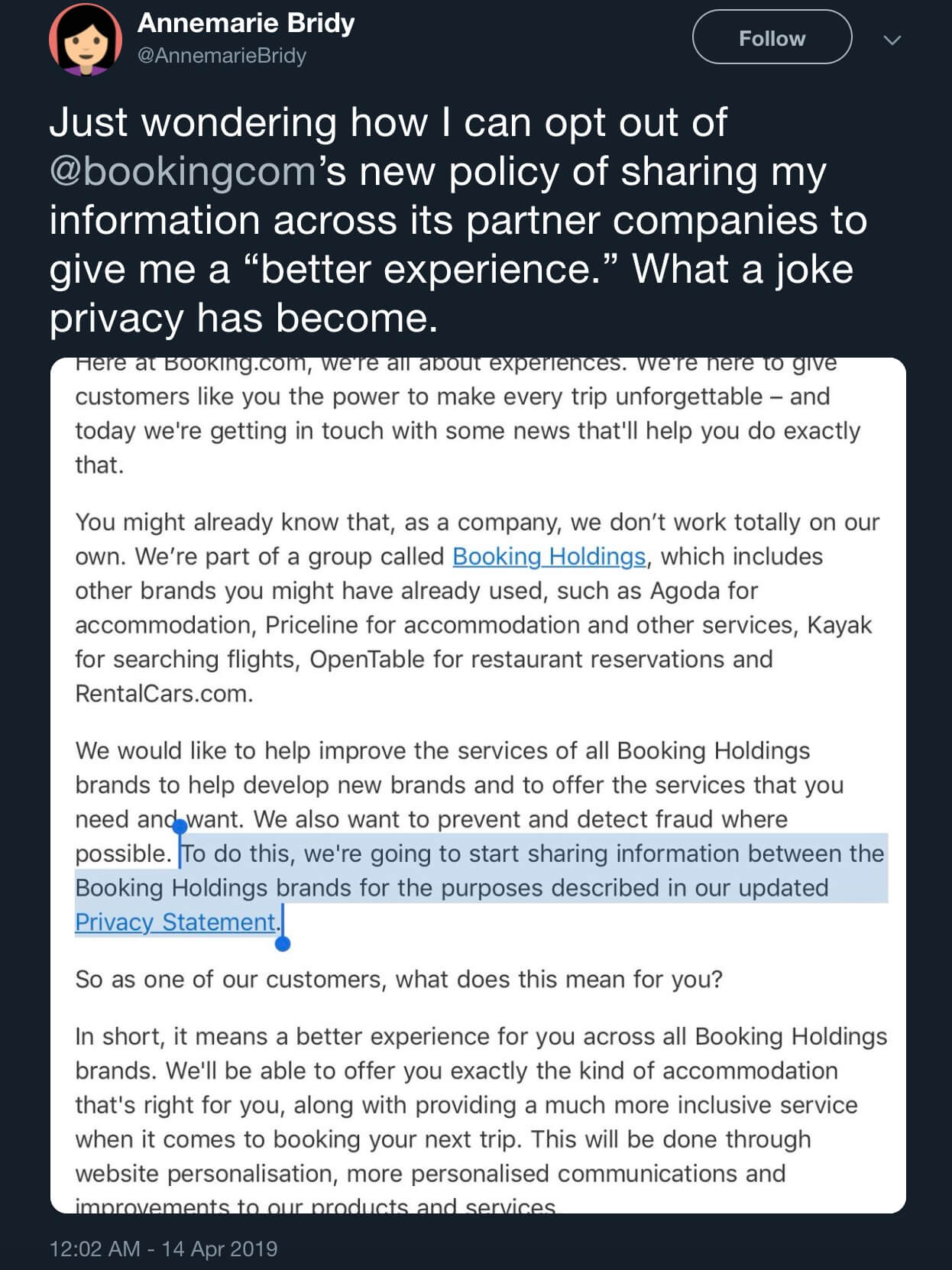
“Just wondering how I can opt out of @bookingcom’s new policy of sharing my information across its partner companies to give me a “better experience.” What a joke privacy has become.”
The tweet is in reference to Booking.com’s new update to their privacy policy announcing yet more sharing data with 3rd parties: “…we’re going to start sharing information between the Booking Holdings brands for the purposes described in our updated Privacy Statement.”
It seems that travel companies seem to be moving towards more tracking at a time when it’s getting scrutinized more than ever.













