U.S. government websites are affected by a flaw enabling anyone to generate URLs that redirect to external websites with their domains – a perfect tool for bad actors to spread malware and acquire personal information.
The issue was first reported by Gizmondo a year ago. A wide variety of U.S. government sites were misconfigured, allowing porn bots to generate links that redirected users to hard-core porn sites. Among the websites affected there is the Justice Department’s Amber Alert site, of which links redirected to erotic material.
Some government offices addressed the problem by changing the settings following Gizmodo’s report. Unfortunately, the problem persists and is affecting several new websites. It seems that the porn bots are preying on the poorly configured sites, creating a serious security issue.
Masquerading malicious links to appear official can be a useful tool in the hands of cyber-criminals. The redirects may be used for conducting phishing campaigns, encouraging the user to hand over personal information such as names, addresses, and other sensitive data.
A report that appeared last week on StateScoop reported that a foreign hacker created some fake versions of government websites across the U.S. to steal information from small and medium-sized companies. The fake websites mimicked those belonging to officials in San Mateo-California, Tampa-Florida, North Las Vegas-Nevada, and Dallas County, Texas.
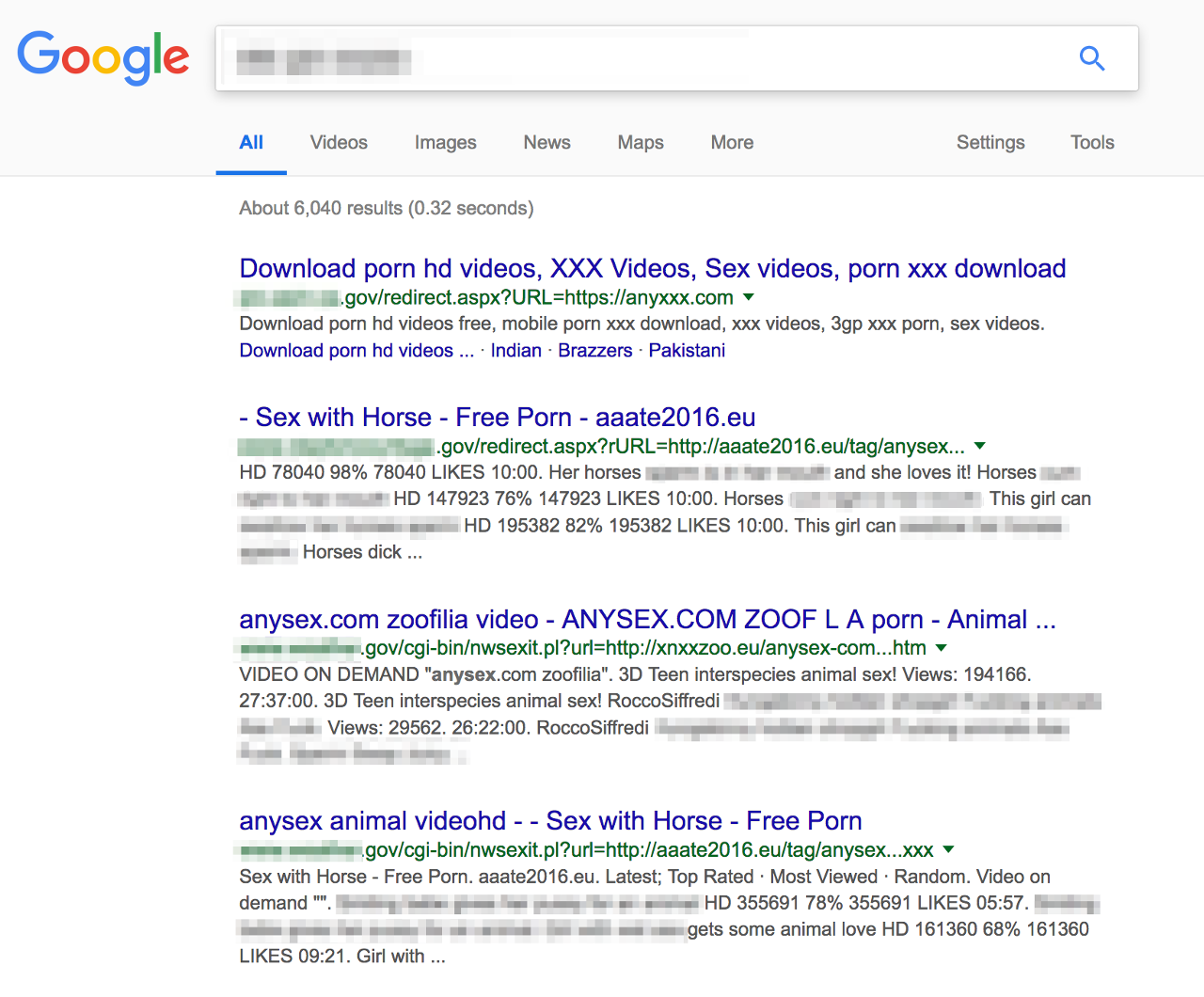
Google continues to index redirects from government domains that send users to pornographic content. A redirect from Whistleblowers.gov points users to “Free Extreme Brutal Porn Videos.” A link from the Department of Health website Heathfinder.gov directs users to a “Menage A Trois With Russian Teen Babe” video.
This technique – presumably used in an attempt to boost search rankings – could be theoretically used to redirect to websites hosting malware.
According to David Maass, an investigative researcher at the EFF, “this isn’t a problem that requires a cybersecurity contractor to discover.”
“It just comes up through some fairly basic Google searches,” says Maass. “I was able to turn up several dozen agencies in just about 20 minutes of searching. I don’t think it’s a particularly hard problem to fix.”
“What makes it worse is that even after this issue was reported in a national news outlet, it still didn’t trigger a review,” he added.
Gizmodo is currently trying to contact as many affected government agencies as possible.













