Famed ethical hacker and former head of Twitter security Peiter “Mudge” Zatko has accused Twitter of allowing foreign intelligence agencies to penetrate the platform multiple times and alleges that in one instance, the company even hired government agents who “would have access to vast amounts of Twitter sensitive data.”
Mudge made the revelations in a whistleblower disclosure that was sent to Congress and federal agencies last month and first reported on by CNN and The Washington Post.
According to CNN, the full disclosure totals around 200 pages. 84 of these pages have been made public in redacted form along with 55 pages of supporting documents.
Mudge’s most substantial claim in relation to foreign intelligence penetration is that “the Indian government forced Twitter to hire specific individual(s) who were government agents, who (because of Twitter’s basic architectural flaws) would have access to vast amounts of Twitter sensitive data.” Not only does Mudge claim that Twitter hired Indian government agents but he also alleges that Twitter executives were “knowingly permitting an Indian government agent direct unsupervised access to the company’s systems and user data.”
In addition to making specific claims about Indian government agents working for the company, Mudge also alleges that “Twitter received specific information from a U.S. government source that one or more particular company employees were working on behalf of another particular foreign intelligence agency.”
Additionally, Mudge’s redacted disclosure describes multiple instances where Twitter’s relationship with foreign entities had “harmed free expression” and potentially allowed foreign entities to gain access to sensitive user data.
One of these instances revolved around alleged concerns within Twitter that Chinese entities, who had paid money to Twitter, could receive information that would allow them to identify and learn sensitive information about Chinese users who had successfully circumvented China’s block on Twitter and other users around the world.
“Twitter executives knew that accepting Chinese money risked endangering users in China (where employing VPNs or other circumvention technologies to access the platform is prohibited) and elsewhere,” the disclosure states. “Twitter executives understood this constituted a major ethical compromise. Mr. Zatko was told that Twitter was too dependent upon the revenue stream at this point to do anything other than attempt to increase it.”
Another of these alleged instances involved current Twitter Chief Executive Officer (CEO) Parag Agrawal when he was serving as Twitter’s Chief Technology Officer (CTO). Mudge claims that “Agrawal suggested to Mudge that Twitter should consider ceding to the Russian Federation’s censorship and surveillance demands as a way to grow users in Russia” a few months before he was promoted to CEO.
“Although Mr. Agrawal’s suggestion was never pursued or implemented, the fact that Twitter’s current CEO even suggested Twitter become complicit with the Putin regime is cause for concern about Twitter’s effects on U.S. national security,” the disclosure states. “This was a strong departure from the message Mr. Dorsey had conveyed to Mr. Zatko.”
A third instance described by Mudge in the redacted disclosure involves the Nigerian government. According to Mudge, Twitter made a “deliberate decision” to refrain from correcting false claims about “non-existent discussions” between the Nigerian government and Twitter executives after Nigeria blocked Twitter in June 2021. Mudge alleges that this allowed the Nigerian government to “impose various conditions on the platform” which “harmed free expression rights and democratic accountability for Nigerian citizens.”
Not only does Mudge raise concerns about foreign government infiltration and surveillance but he also claims that “Twitter employees were repeatedly found to be intentionally installing spyware on their work computers at the request of external organizations.” Mudge adds that Twitter only learned of this by accident or because of employee self-reporting.
“It was repeatedly demonstrated that until Twitter leadership would stumble across end-point (employee computer) problems, external people or organizations had more awareness of activity on some Twitter employee computers than Twitter itself had,” the disclosure states.
These are just some of the many assertions that Twitter’s former head of security makes in the documents. He also claims that around half of Twitter’s employees were given access to “sensitive live production systems and user data,” that many of Twitter’s servers are unable to support encryption at rest, and much more.
Four documents have been made public:
- Mudge’s 84 page redacted whistleblower disclosure. You can view the redacted disclosure here.
- A cover letter to the disclosure that was prepared by Whistleblower aid, a group representing Mudge. You can view the cover letter to the disclosure here.
- A document where Mudge detailed his concerns with Twitter’s security after being terminated. This document was produced after Twitter asked Mudge to spell out his issues with Twitter’s security so that it could investigate. You can view this document here.
- A document on Twitter’s capabilities to counter “misinformation and disinformation.” Mudge commissioned an outside firm to produce this document during his first year as Twitter’s head of security. You can view this document here.
Mudge joined Twitter on November 16, 2020 and was fired on January 19, 2022. Twitter claimed he was terminated for poor performance while Mudge argues that he was fired for “pushing improvements from the inside.”
Twitter responded to Mudge’s claims by describing the disclosure as “a false narrative about Twitter and our privacy and data security practices that is riddled with inconsistencies and inaccuracies and lacks important context.”
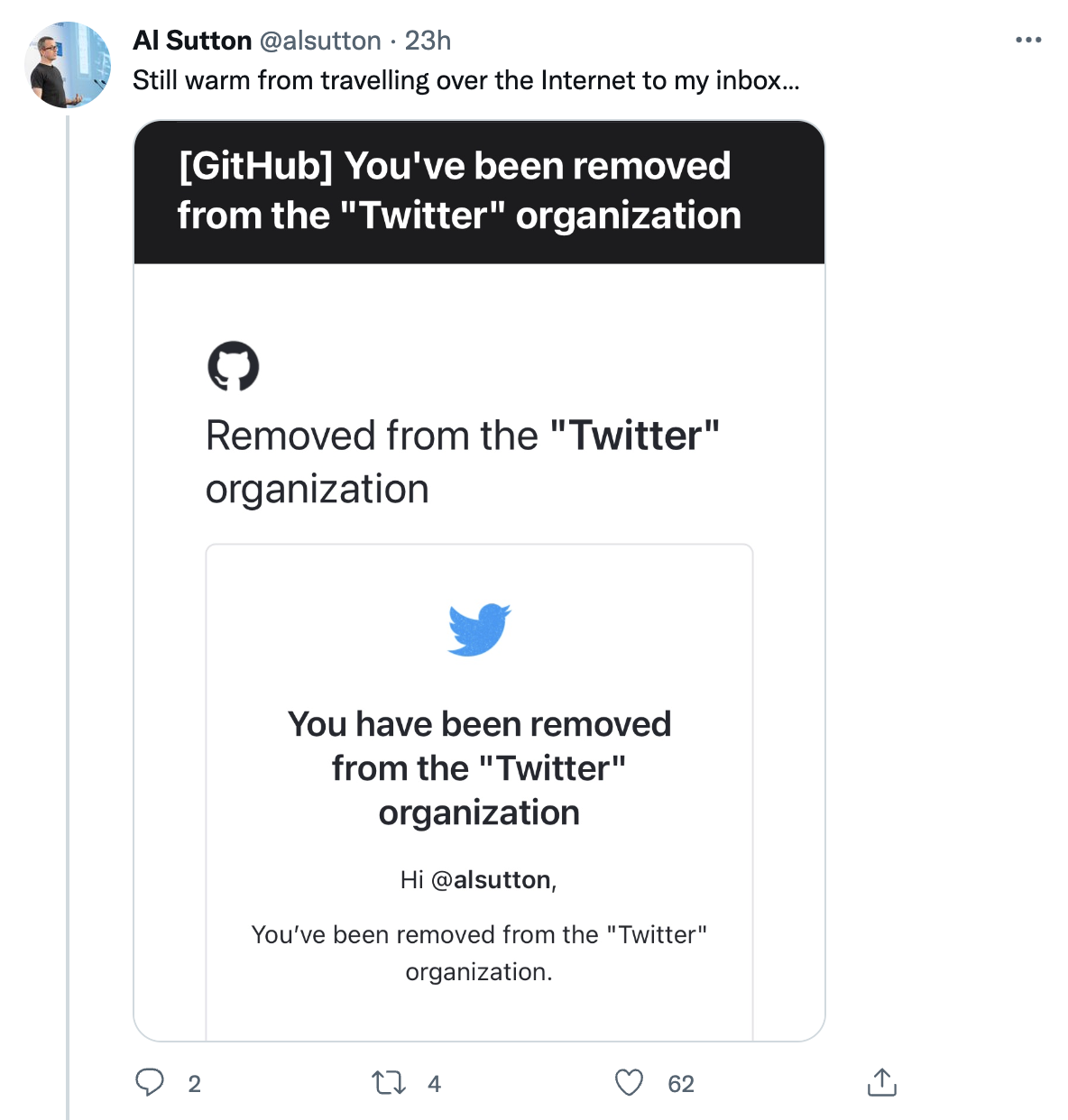
Shortly after the release of Mudge’s redacted disclosure, Al Sutton, a former Twitter employee revealed that he still had access to the Twitter GitHub committers group, 18 months after being let go from the company.
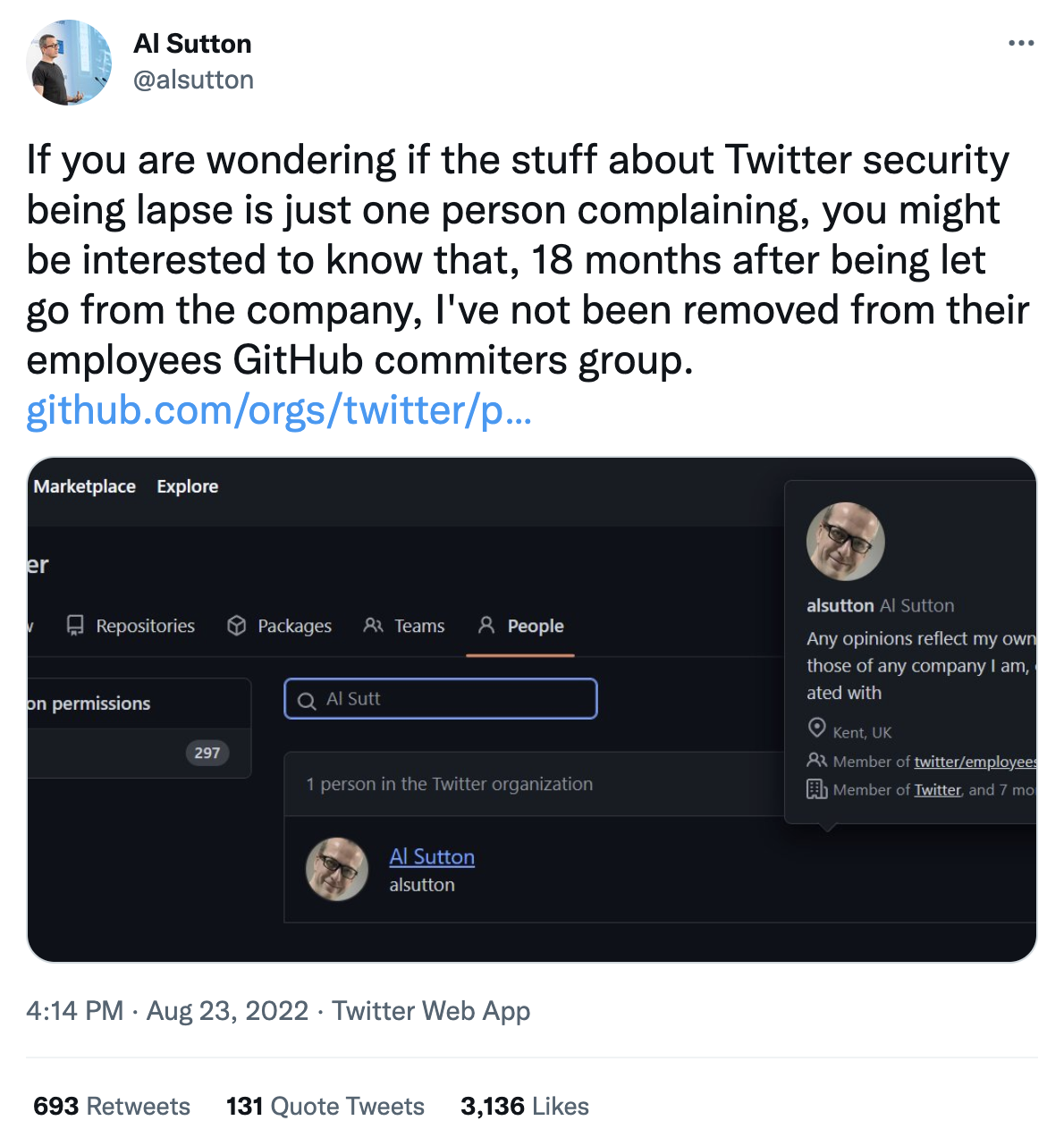
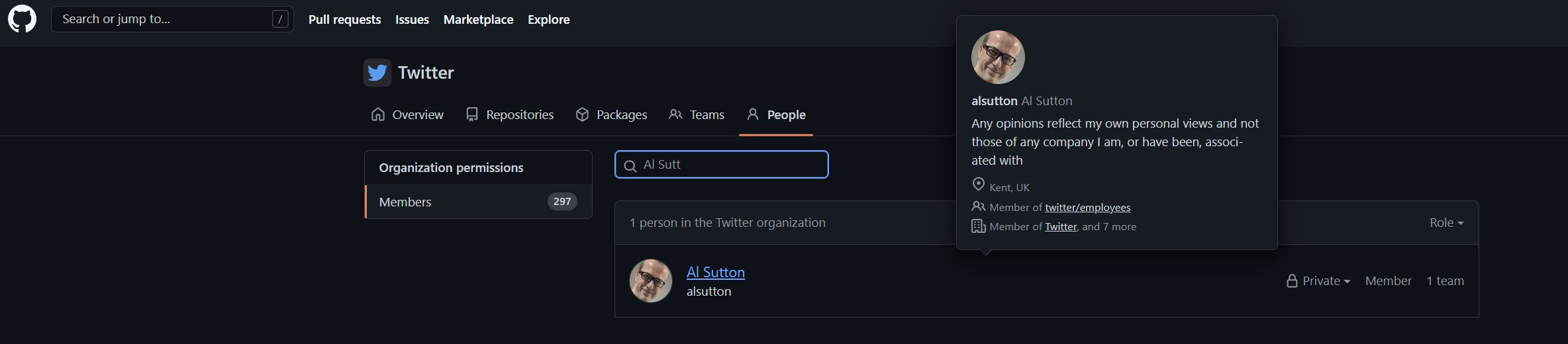
Sutton also claimed that he had access to a “private, active” Twitter GitHub repo during these 18 months.
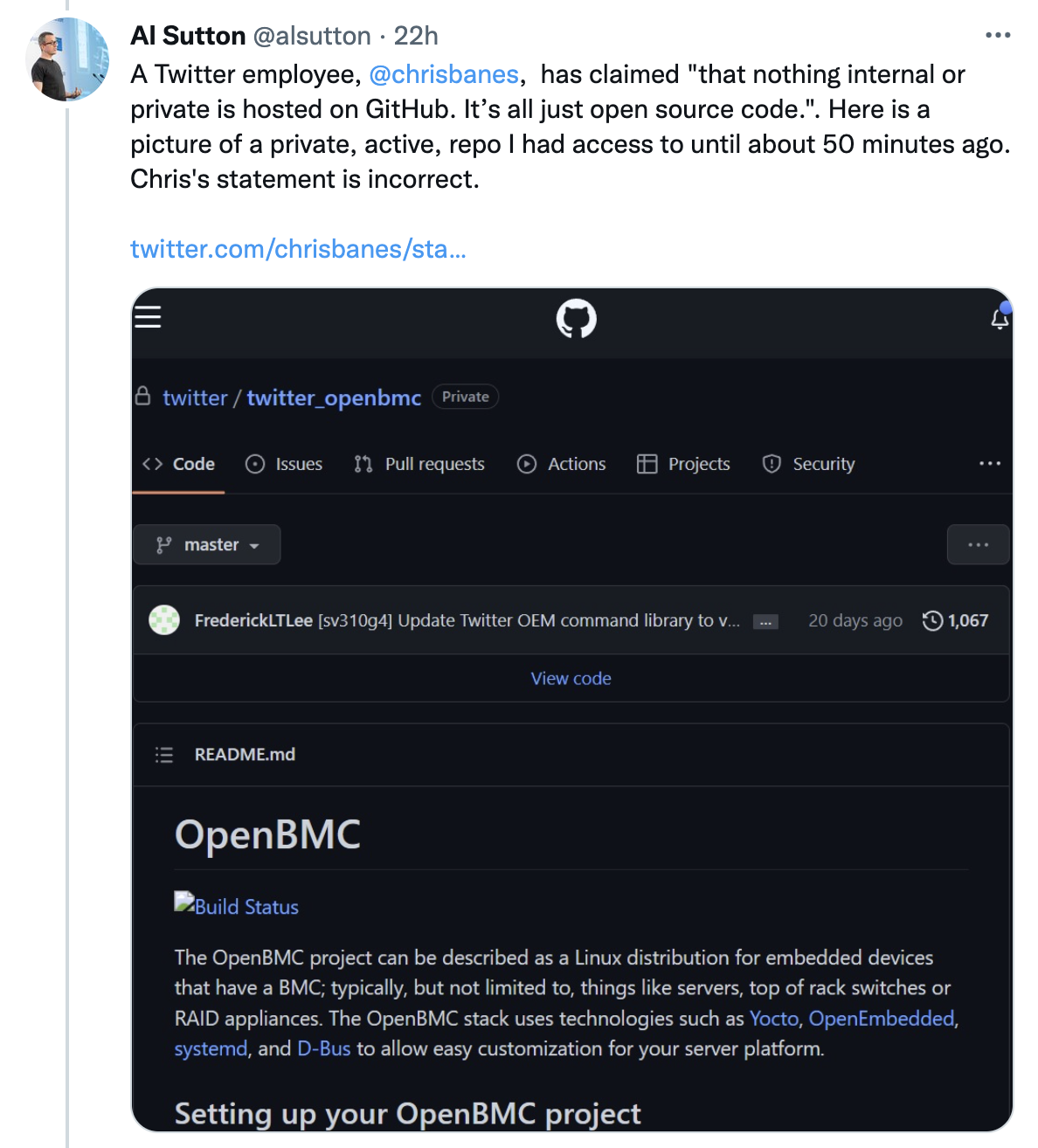
“It gives me access to their private repositories on GitHub,” Sutton said. “This is not where they store their main source code, but some projects are not public.”
Sutton noted that having this access left him with “access to the private and public membership list of the group which could have been used as a social engineering starter list (33 public, 267 private).”
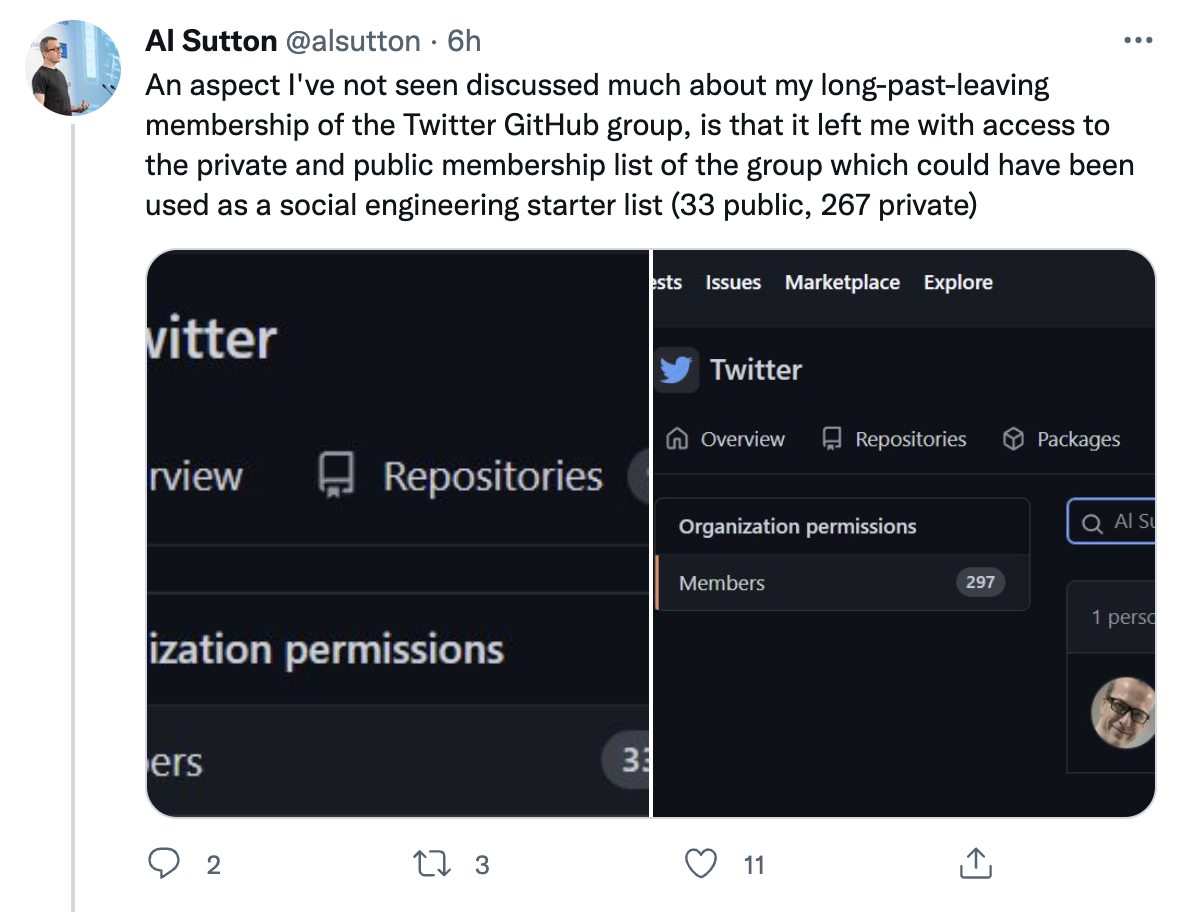
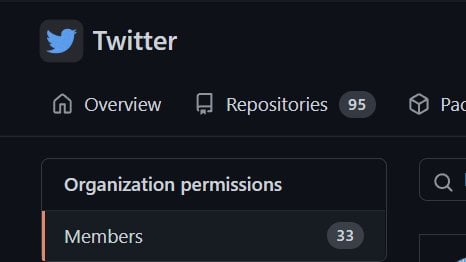
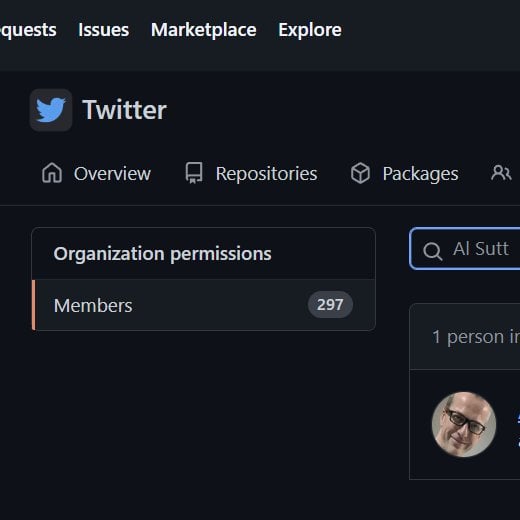
After Sutton posted publicly about still having access to this GitHub group, Twitter removed his access.
Twitter Staff Software Engineer Chris Banes responded to Sutton’s tweet about having access to a private, active Twitter GitHub repo by claimed that Sutton had “just posted a screenshot to a fork of an open source project.”
Mudge’s revelations comes just a few weeks after an ex-Twitter employee was found guilty of using his position at Twitter to spy on Saudi dissidents.
Twitter has previously suffered numerous profile hacks and in the wake of these hacks, regulators and former employees have often pointed to the sweeping access employees have to Twitter’s administrative tools and user data.
In 2009, hackers gained access to Twitter employees’ administrative accounts in two separate incidents and used this access to reset passwords and send unauthorized tweets. One of these unauthorized was sent from the account of then-President-elect Barack Obama.
After these hacks, the Federal Trade Commission (FTC) claimed that almost all of Twitter’s employees could access Twitter’s administrative tools and that these tools could have been used to take over user accounts, reset passwords, and send tweets on behalf of users.
The FTC charged Twitter for failure to safeguard personal information in the wake of these 2009 hacks and Twitter subsequently settled with the FTC. Under the terms of this settlement, Twitter was required to implement a comprehensive information security requirement and comply with various reporting requirements.
Mudge addresses this settlement in his disclosure and claims that highly-experienced experts who reported to Mudge while he was at Twitter told him that “Twitter had never been in compliance with the 2011 FTC Consent Order, and was not on track to ever achieve full compliance.”
In 2020, Twitter was the subject of the largest hack of a social media platform in history which resulted in hackers taking over and sending unauthorized tweets from numerous high-profile Twitter accounts including those of former President Obama, then-presumptive Democratic presidential nominee Joe Biden, Tesla and SpaceX CEO Elon Musk, and then-Amazon CEO Jeff Bezos.
Following these 2020 hacks, two former Twitter employees claimed that more than 1,000 employees had access to internal Twitter tools that could change user account settings and give control of accounts to others.
Sutton, the former Twitter employee who had access to Twitter’s GitHub 18 months after he was let go, also noted that his access to information that could have been used as a social engineering starter list is “particularly relevant…because social engineering is the technique widely believed to have been used in the 2020 incident when 100+ high profile accounts were compromised.”
“Leaving ex-employees, particularly potentially disgruntled ones who have been ‘let go,’ with access to this potentially high-value list for a year and a half seems a big oversight in corporate security, and is one of many reasons why I have no reason to doubt @dotMudge’s [Mudge’s] claims,” Sutton tweeted.
Mudge is due to take part in closed-door Capitol Hill briefings this week and numerous lawmakers have called for the FTC and US Justice Department to investigate Twitter after Mudge’s disclosure was made public.













