On the heels of the news that the Department of Homeland Security is considering outsourcing surveillance of US citizens’ social media after the January 6th riot, a new report has revealed some of the consequences of building databases on citizens: that data can leak.
A secret terrorist watchlist containing 1.9 million records, including “no-fly” status, was exposed online. It is possible, but not stated, that bad actors came across the list, as it was passwordless and searchable on a couple of search engines.
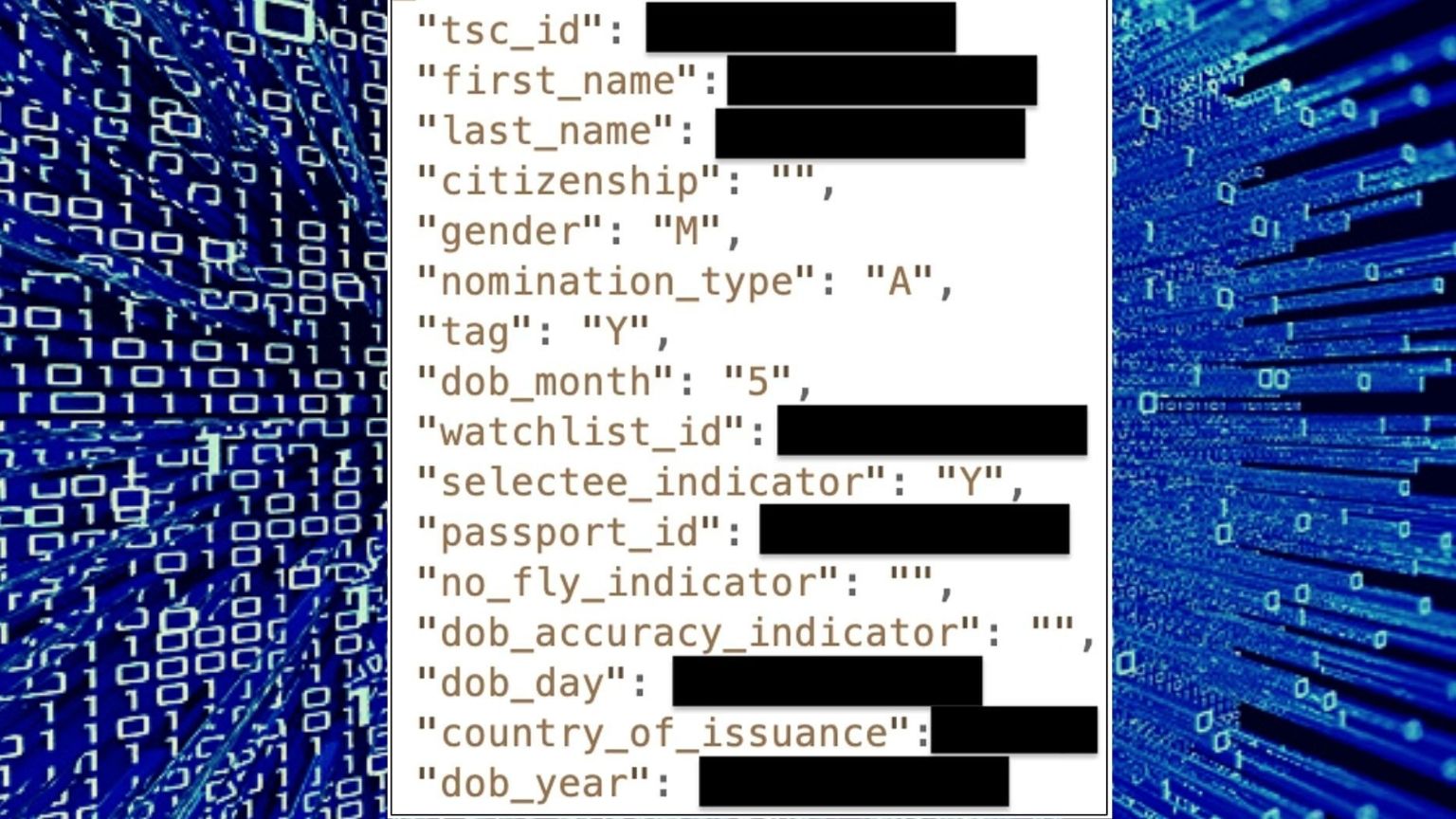
Bob Diachenko of Discovery Research stumbled on the list in an open Elasticsearch cluster in July this year. He claims that the list had the sensitive information of more than 1.9 million people, including their names, nationality, date of birth, gender, no-fly status, and passport details.
Diachenko concluded that it was a no-fly list or a similar terrorist watchlist because it contained fields such as “no_fly_indicator” and “passport_id.”
“That was the only valid guess given the nature of data plus there was a specific field named ‘TSC_ID’,” Diachenko told BleepingComputer. TSC could stand for Terrorist Screening Center, a resource of the FBI used by multiple agencies for counterterrorism purposes. The TSC has a database, called the Terrorism Screening Database or the “no-fly-list.”
Diachenko is probably not the only person who stumbled on the list, considering it did not require a password to access, and it was searchable on the search engines ZoomEye and Censys.
Diachenko discovered the database on July 19 on a server with an IP address from Bahrain. He reported the data leak to the Department of Homeland Security on the same day, but claims it took the department three weeks to remove it. “I discovered the exposed data on the same day and reported it to the DHS….The exposed server was taken down about three weeks later, on August 9, 2021…It’s not clear why it took so long, and I don’t know for sure whether any unauthorized parties accessed it,” Diachenko wrote in his report.
According to the researcher, it would be dangerous for the people in such a list if it landed in the wrong hands.
“In the wrong hands, this list could be used to oppress, harass, or persecute people on the list and their families,” explained Diachenko. “It could cause any number of personal and professional problems for innocent people whose names are included in the list.”