Google recently urged account owners to start using their mobile phones as a means to protect themselves from hijacking attacks and automated bots, phishing and attempted targeted attacks.
These attempted attacks which happen everyday target email address because it is at the center of everyone’s life as it is used for creating web service accounts as well as for receiving communication. Hence, Google and other big companies have invested so much on establishing a single sign-in system for all their web service accounts.
According to a published report, the use of a phone number is the most effective way of fighting off account takeover. This is especially true if the account has not been targeted by hackers yet.
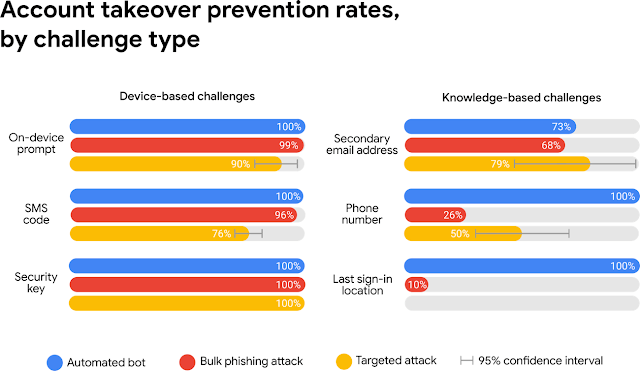
Findings of the said report show that the success rate of a takeover on accounts linked to phone numbers is as high as 100% with automated bots, 99% with the usual phasing attacks, and 90% with targeted attacks. This is based on the study of 350,000 real-world hijacking attempts on a 1.2 million account owners.
Attempted attacks whether from automated bots, bulk phishing or targeted accounts can be prevented with the use of on-device prompt. This is a protective measure that authorizes the login by confirming it on the phone.
In addition, preventing the attacks is even more successful when done by authorizing the login with the use of a security key. If enabled, this prevents all account takeover attacks (ATA) since it requires the physical presence of the phone to continue the login process.
The report also identified the use of SMS-based authentication to be the weakest way of preventing attacks. This method can be easily beaten by a hacker who is in a man-in-the-middle position as well as opens up the risk of sim-swapping. The hacker can easily deploy phishing attack and intercepts validation requests.
Google urges account holders to link or set up their phone as a recovery method for their accounts. This may be less convenient for the average user but eventually, it will be a more effective way of protecting accounts against takeover attacks.