An Indian healthcare data surveillance platform was exposed to the internet for over a month, despite several warnings from investigators.
Security researchers Noam Rotem and Ran Locar took to VPNMentor’s blog with their findings.
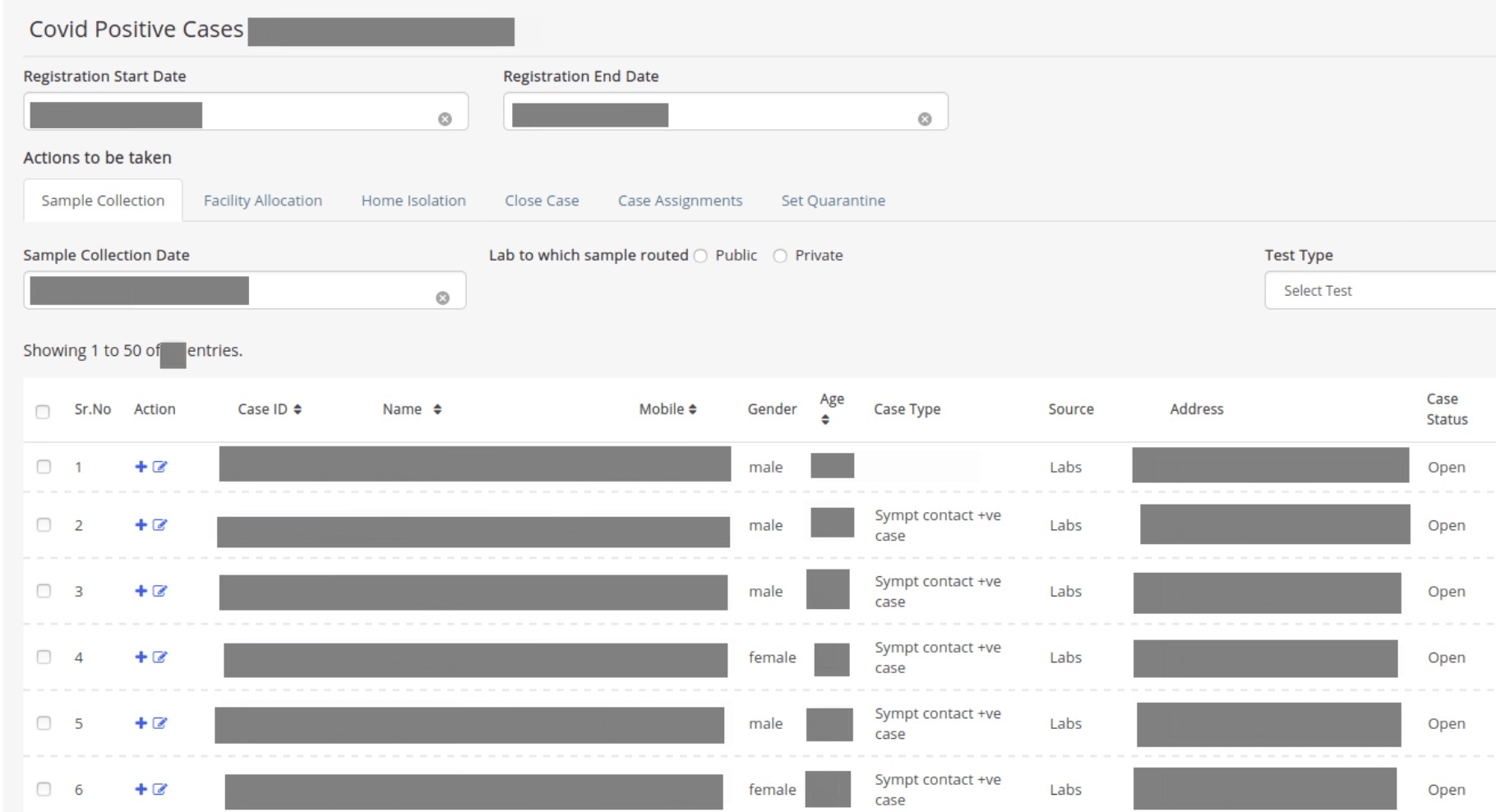
On the first of August, they discovered an Indian surveillance platform that served as the backend for a COVID-19 track and trace app made by the government. The platform included a database with over 8 million records of COVID-19 test subjects – belonging to presumably every person that has received COVID-19 testing in the Indian state of Uttar Pradesh – and stored this information on a public-facing online server, unencrypted with no password or other credential access required.
To make matters worse, the unsecured git repository even included a data dump with admin login credentials. Meaning an attacker could have easily obtained complete access over the system.
The team claims to not have accessed it for themselves, but they have confirmed the authenticity of the admin passwords and that they did in fact allow access into the platform’s admin dashboard.
The security researchers tried to contact the Uttar Pradesh government since August 10th, but it wasn’t until three days after they contacted India’s Computer Emergency Response Team (CERT-In) for the third time that the breach was secured.
They initially contacted the Israeli embassy in India on August 10th, the day after analyzing the breach. The Israeli embassy was asked to forward their report to CERT. After more than two weeks with no response, they contacted CERT directly as well as Uttar Pradesh’s Cybercrime police department.
On September 7th, they contacted CERT directly again. Only then, it seems, that their communications were read – as the breach was secured three days later.
It seems as though no thought whatsoever was put into the security of a platform that would be handling such sensitive personal data. Aside from the negligence of leaving the server publicly-facing and the data unencrypted, the fact that admin login credentials were left there for anyone to download is the epitome of incompetence.
About those admin credentials… the passwords were encrypted using the very basic and easily crackable MD5 algorithm that is hardly considered encryption by modern standards. Funny enough, a malicious attacker wouldn’t even need to crack the password, as the unencrypted version was stored right next to the encrypted one in a separate column. At that point, why even bother using “encryption”?
Even the passwords themselves were embarrassing – many consisting of nothing more than 4 digit numbers. For some context, the “strongest” four digit password I could come up with can be cracked in 200 nanoseconds, according to howsecureismypassword.net. A lot of those 4 digit passwords were even the same as the account number, meaning they could be easily guessed without even needing to crack them.
What’s more chilling is the personally identifying information (PII) not of the admins, but of those who decided to do the responsible thing and get tested for COVID-19. The database shows all sorts of information including names, gender, age, address, mobile phone number, date of arrival to India, “date of tracking”, along with their symptoms such as “Soar Throat”, fever, dry cough, breathing problem, and whether any action was taken in that person’s case.
Further information included prior medical records, how the patient came in contact with COVID-19 (more specifically, whether they’ve traveled outside the country recently), and where they’ve been isolating during the quarantine.
Records were also not limited to Indian nationals. Non-Indians who got tested in India are potentially at risk of having their personal information exposed. Many foreign healthcare workers are in the database as well.
An unsuspecting person receiving a request for more personal information (phishing) or even some kind of payment for an alleged treatment would have no reason to suspect that anyone other than the Indian clinic or doctor that tested them is aware of their symptoms or diagnosis.
For all its faults, incidents like this remind us of the importance of Europe’s GDPR. It specifically mandates that private companies and governments alike handle PPI using modern security practices, and makes them responsible in the event of a breach.
India is no stranger to privacy and other human rights violations relating to the internet.
If you're tired of censorship and dystopian threats against civil liberties, subscribe to Reclaim The Net.