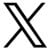The Twitter account for BigJigglyPanda, a popular video game streamer with over 500,000 Twitter followers, was hacked after another alleged AT&T error. The hack also appears to have been perpetrated by the same hacking group that seemed to be behind the hacks of Shane Dawson and other YouTubers last week.
The account was compromised for over seven hours and the hackers posted a series of doxes, threats, and racist tweets while in control of the account. Many Twitter users brought the compromised account to the attention of Twitter support during these seven hours but the tweets posted by the hackers were only recently scrubbed from the BigJigglyPanda Twitter account.
Click here to display content from Twitter.
Learn more in Twitter’s privacy policy.
Click here to display content from Twitter.
Learn more in Twitter’s privacy policy.
Like with the many of the previous YouTuber hacks, the Twitter account for BigJigglyPanda had its bio changed to contain the hashtag #ChucklingSquad and linked to a Discord server which appeared to be controlled by the hacking group. These were hallmarks of the previous hacks and suggest that the same group is behind the hack of BigJigglyPanda’s Twitter account.
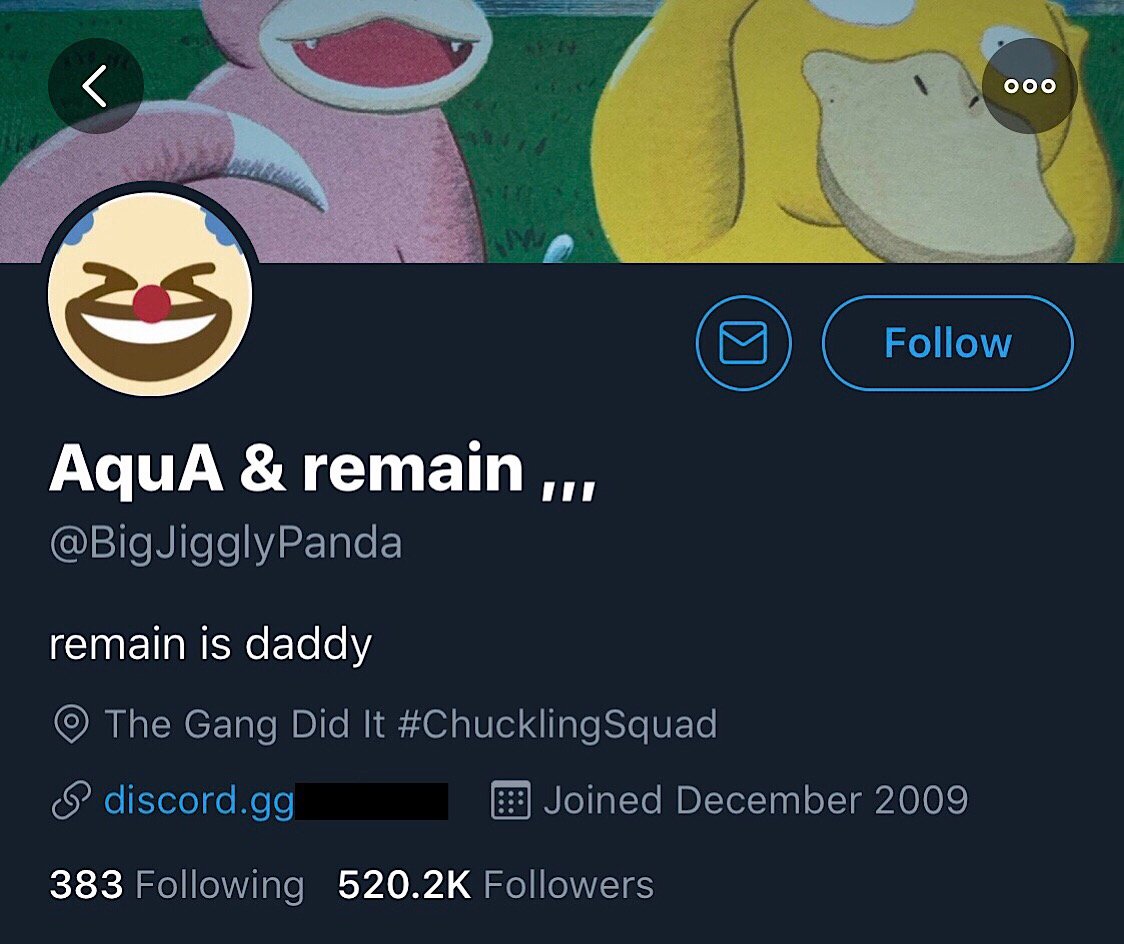
Another thing that’s similar to the previous hacks is that the carrier AT&T has been accused of being responsible for letting the hackers gain access to BigJigglyPanda’s Twitter account. In a series of tweets that appear to have been posted by the real BigJigglyPanda while he had briefly regained control of the account, the following text was posted:
“My 1st time being hacked never thought I’d be a victim in one of these attacks I’m such a nice guy I don’t see why I was a target furthermore @ATT really needs to fix the security these guys have hacked numerous of content creators and are still doing it. Time to switch carriers
Because of @ATT Hackers have stolen $20,000 and stole personal belongings of mine I am in shock right now and I don’t know what to do.”
The account is now hidden behind a “sensitive content” warning with the altered bio and hacker’s tweets removed.
Besides the allegations against AT&T, the recent wave of Twitter account takeovers also points to issues with Twitter’s security. Not only did it take seven hours for Twitter Support to resolve this issue, despite the account being mass flagged and mass posting content that violates Twitter’s policies, but its two-step verification setup also creates potential security problems by requiring users to add a phone number to their account.
Twitter forces users to add a phone number to their account, even if they’re verifying the account through other means such as a mobile security app or a physical security key. If users try to remove the phone number after selecting an alternative verification method, Twitter disables two-step verification on the account. Twitter says: “This requirement is in place for account recovery.”
However, if a hacker manages to gain control of a phone number via SIM swapping, a process where hackers contact a carrier and convince them to switch the phone number to a SIM card that they control, they can use this account recovery process to gain control of Twitter accounts.
Twitter isn’t the only company where accounts can be compromised as a result of SIM swapping. In May, a group of hackers used SIM swapping to steal more than $2.4 million worth of cryptocurrencies.
According to research from Google, SMS code verification is one of the weakest forms of device-based account protection and only has a 76% chance of preventing account takeovers. In other words, around one in four targeted account takeover attempts will be successful if the account uses SMS code verification. Google’s research also shows that a physical security key is the most effective tool for protecting online accounts and has a 100% success rate when it comes to preventing account takeovers.
Despite these statistics, many online service providers don’t support physical security keys. Even those that do offer support for physical security keys, such as Twitter, often force users to have a phone number for account recovery which makes the protection that the security keys provide redundant.
If you're tired of censorship and dystopian threats against civil liberties, subscribe to Reclaim The Net.