The notorious Chuckling Squad hacking group, which hacked Twitter CEO Jack Dorsey five days ago and multiple YouTube and social media stars last month, appears to have struck again, this time briefly gaining control of actress Chloë Grace Moretz’s Twitter account.
Moretz’s account was compromised for less than an hour but during that time, the hackers sent out tweets containing the phrase “Chuckling rn” and #chucklingSquad – the same phrases and hashtags were used in tweets sent from accounts that have previously been hacked by Chuckling Squad.
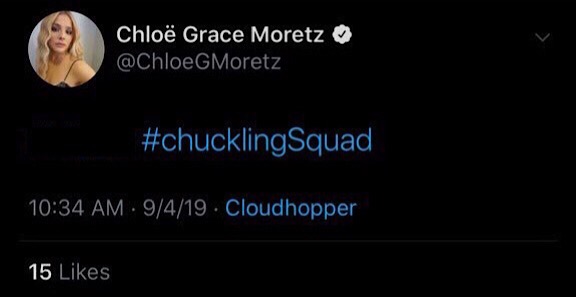
Another similarity with the previous hacks was that the tweets posted by the hackers contained racist language, threats, and doxes. Some of the tweets also contained links where the hackers claimed to have posted nude celebrity photos.
The tweets from the hackers were also posted by Cloudhopper – the same Twitter-owned service that the hackers used to post tweets to Dorsey’s account when it was compromised. Cloudhopper was acquired by Twitter in 2010 and allows tweeting by SMS. When Dorsey’s Twitter account was compromised, some Twitter users alleged that Cloudhopper was hacked and this was how the hackers managed to send tweets from Dorsey’s accounts.
While Twitter didn’t directly confirm that Cloudhopper was breached, Twitter comms alluded to it in an update on Dorsey’s account being compromised by saying an oversight by Dorsey’s mobile provider “allowed an unauthorized person to compose and send tweets via text message from the phone number.”
Click here to display content from Twitter.
Learn more in Twitter’s privacy policy.
The news of yet another Twitter account breach adds to the growing concerns people have about Twitter security and the requirement for users to provide their phone numbers in order to enable two-factor authentication.
This requirement leaves Twitter users susceptible to SIM swapping – a technique where hackers convince a mobile carrier to switch a targets phone number to a SIM card that they control.
Once hackers have control of this phone number, they can gain access to Twitter accounts or at least sent tweets from these accounts by either triggering the account recovery process or using a phone number based service which is what appears to be happening with the tweets sent from Cloudhopper. Most of the recent Twitter hacking victims have said that SIM swapping was what led to their account being compromised.
While the rise in high profile Twitter account hacks shines a light on Twitter’s security issues, the larger issue is phone numbers being used for account verification. The same SIM swap technique that has been used to recently gain control of these Twitter accounts can also be used to gain control of any other online account that relies on a phone number for verification.
If you're tired of censorship and dystopian threats against civil liberties, subscribe to Reclaim The Net.